What is Phishing?
Phishing, vishing, and smishing are some of the favorite tools for cybercriminals worldwide. They use these methods to gain access to your sensitive information in hopes of stealing your identity, your personal information, or your financial assets.
Not sure whether an email is a phishing scam? Check out the VCU PhishingNet to see if it has been reported and verified as a scam!
What is Phishing?
Phishing is a technique where a cybercriminal tries to gain access to a victim's personal information through a scam email. These emails or links contained in these emails typically ask for the victim's
- Name
- Social security number
- User name
- Password
- Credit Card number and expiration date / CCV code
The end goal for the cybercriminal is to gain access to the personally identifiable information of the victim and either sell the information or use the information to commit crimes.
Protect yourself by ensuring the legitimacy of an email before responding to or clicking on any included links or attachments. Be cautious of emails requesting any of the above information.
Visit our phishing alert page for updates on the latest scams affecting the University.
How do I Identify Phishing Emails?
The attackers typically leave some telltale signs in phishing scams. The following examples will show you how to identify phishing emails with these telltale signs:
Phishing Email Example 1:
From: administrator@vcu.edu.cn
To: youremail@vcu.edu
Dear youremail,
We are shut down your email due to possible hacking. Please reply to this email with your cridentals below:
Name: _______________
Email Address: _______________
Password: _______________
Credit card number: _______________
Credit card type: Visa MasterCard AmEx Discover
Expiration Date: _______________
CCV value: _______________
The "phishing" signs in this email are:
- The sender claims to be from administrator@vcu.edu.cn. VCU.EDU is the origin of VCU email addresses, but VCU.EDU.CN is not. Email addresses from VCU should always end in VCU.EDU.
- The email used poor grammar and spelling, such as "We are shut down..." and "critentals". Poor grammar and spelling are usually signs of scam and phishing emails.
- Finally, this email asks you to send your password, credit card number, expiration date, and CCV value, etc. Any legitimate company will never ask you to send such information over email. You should never send this information via email, or a link contained in an email unless you are the person who initiated the transaction.
Phishing Email Example 2
From: somoneyouknow@gmail.com
To: youremail@vcu.edu
Hi,
My regrets for this sudden request, I have been involved in a robbery during my trip to Madrid, Spain. I got mugged and all my belongings cash, mobile phone and credit cards were all stolen at gun point. I need your help as am trying to raise some money.I have made contact with my bank but they are not providing a fast solution. I need you to lend me some money to sort my self out of this predicament, will pay back once I get this over with.Please let me know if you can assist me in anyway so i can forward you details to effect a transfer. You can reach me via email or the hotel's desk phone+3491XXXXXX95.
The "phishing" signs in this email are:
- This email is a bit more sophisticated, and unsuspecting people may fall for it
- First, make sure you know the sender, if you don't know the person, then this is definitely a scam.
- Second, if you know the person, call him or her and make sure they are indeed out of the country. Many of the scammers will simply compromise a victim's account and send phishing scam to everyone in the victim's address book.
- You should not contact the phone number provided unless you are sure that the person is indeed out of the country and in trouble.
Phishing Email Example 3
From: ITsupport@vcu.edu
To: youremail@vcu.edu
Dear youremail,
Due to inactivity in your account, we will deactivate your account in 3 days. If your account needs to remain active, then please follow the link below and verify your identity:
Click here to log in
System Administrator
When you click on the link, you see the following screen pop up:
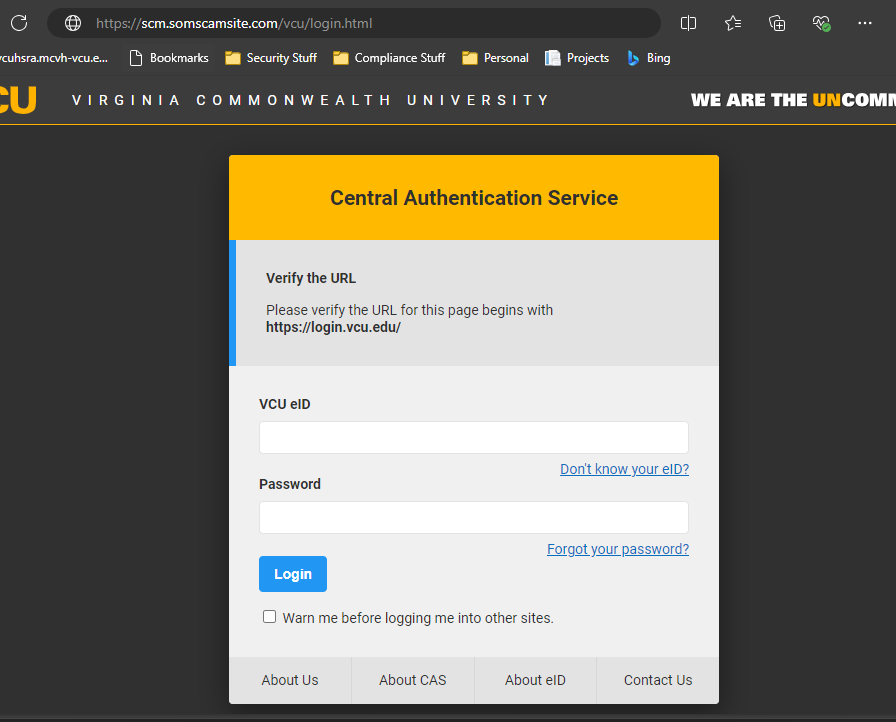
The "phishing" signs in this email are:
- First, you should always question the email if the email contains a link. You need to ask the following questions:
- Do I know the sender?
- Am I expecting the email?
- Does the link look legitimate? (see URL identification information below)
- If the answer of either of the questions above is "no", you should consider calling the sender and verify that the email is legit, or contact your IT staff or VCU IT Support Center (828 - 2227) to help you verify the legitimacy of the email.
- If you happen to click on the link that was provided and received a page similar to what was shown above, you must look at the URL (address) of the page.
- For input of any sensitive information https:// must be used instead of http://
- Further, the telltale sign of a phishing URL can be observed between http:// or https:// and the first "/"
- In this case, the URL is:
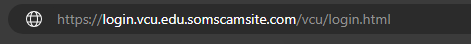
- Note that URL should be read backward, and although mail.vcu.edu is in the URL, what appears right before the first "/" after "http://" or "https://" represents the actual site you are actually accessing. In this case, the website is somescamsite.com, and not vcu.edu
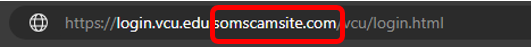
- In this case, the URL is:
Phishing Example 4
From: Wells_Fargo (example@psu.edu)
To: youremail@vcu.edu
Dear Cardholder,
We have completed our ATM/Debit Card software upgrade and determined that an error did occur.It will only take few minutes to re-activate all your Check Cards accounts.Please click the link below to proceed with re-activation process :
http://online.wellsfargo.com.gz51wikqn44vcytW.org/index.php?activatecheckcard=Z8M66
If you have further questions, please call us at 1-800-548-9554. Our hours are (in Pacific Time):
During Daylight Saving Time: Monday - Friday, 5:00 am - 5:00 pm; Saturday, 7:00 am - 4:00 pm.During Standard Time: Monday - Friday, 4:00 am - 4:00 pm; Saturday, 6:00 am - 3:00 pm.
Thank you for bringing this matter to our attention. We hope we have been able to assist you.Sincerely,Wells Fargo Debit Card OperationsYou received this notification because you are a cardholder, account owner, or an authorized representative for this account.
GTPPDXSVHRCNOEYRPXXPSDDVJOYXJVXSTNYKMV
When you click on the link, you see the following screen pop up:
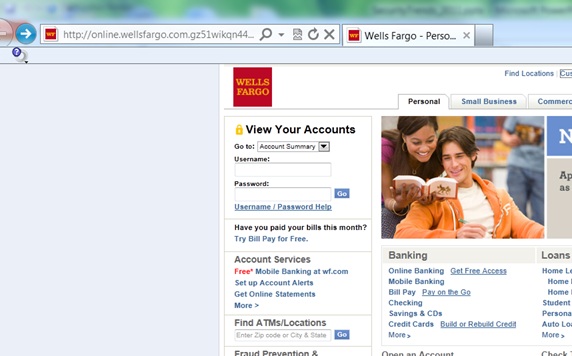
The "phishing" signs in this email are:
- The email looks authentic, however:
- What is an ATM check card / credit card upgrade?
- Is the phone number they provided legit?
- Is the link they provided legit?
- If you happen to click on the link that was provided and received a page similar to what was shown above, you must look at the URL (address) of the page.
- For input of any sensitive information https:// must be used instead of http://
- Further, the telltale sign of a phishing URL can be observed between http:// or https:// and the first "/"
- In this case, the URL is:

- Note that URL should be read backward, and although "wellsfargo.com" is in the URL, what appears right before the first "/", and after "http://" or "https://" represents the actual site you are actually accessing. In this case, the website is gz51wikqn44vcytW.org, and not wellsfargo.com. Further, the site is using http:// instead of https://.

- In this case, the URL is:
Can you identify the bad URLs?
The following are examples of malicious phishing URLs pretending to be a VCU login page, the telltale signs are highlighted in Red.
- http://setup.phunsite.com/vculogin.html - going to phunsite.com instead of VCU
- https://mail.test.vcu.edu.gsdcsfAvxz.get-it.org/login.aspx - going to get-it.org instead of VCU
- https://vcu.edu.ampwny.net/login.htm - going to ampwny.net instead of VCU
- http://www.vculogins.biz/login.asp - this is going to vculogins.biz, which is not vcu.edu
- https://spreadsheet.google.com/vculogin.htm - this is going to google site, not VCU.
Note: Aside from VCU, cybercriminals also pretend to be other institutions to steal your financial and other personal information. We have seen phishing emails pretending to be banks, online merchants, and even the federal or state government.
Spear Phishing
Spear phishing describes a highly targeted phishing attack. Spear phishing is more successful because the message appears to come from a known and trusted individual or organization, contains information which supports its validity and includes a request with a logical basis. The message may address you by name and it may include your job title, phone number or other personal information which was collected from websites or other sources.
Example of a Spear Phishing email:
From: Jon Doe (jsdoe@legitimatesite.com)
To: Youremail@vcu.edu
Dear your name,
Attached is a list of the copyrighted material you are infringing on.As well as hosted at http://legitimatesite.com/copyrights.php under Copyrighted Materials.We are the proprietors of all copyrighted material that is being fringed upon on your companies webste.
We have reserved all rights regarding these trademarked files.Permission was neither asked nor granted to reproduce our copyrighted material, therefore what your company is doing constitutes infringement of our rights.
In terms of the Copyright Statutes, we are entitled to an injunction against your continued infringement, as well as to recover damages from you for the loss we have suffered as a result of your infringing conduct.In the circumstances, we demand that you immediately:
1. remove all infringing content and notify us in writing that you have done so;
2. pay a licensing fee in the amount of 500,000 USD;
3. immediately cease the use and distribution of copyrighted material;
We await to hear from you by.This is written without prejudice to our rights, all of which are hereby expressly reserved.Yours faithfully,Senior Legal AdvisorGraham Barr
Sincerely,
Jon Doe
Legal Counsel
Legitimate Corporation
In this case, no immediate signs can be observed, and the cybercriminal simply wants the victim to click on the link provided in the email. The link will then:
- Install a malicious virus on the victim's computer, and / or
- Collect the victim's credentials via an externally hosted web page, and / or
- Install keystroke logging software or back door that can allow the attacker to spy on the victim.
The phishing emails are hard to identify. However, it is always good to call the sender and verify the legitimacy of the email when it arrives unexpected and contains links.
What do I do when I see Phishing emails?
First, if you are unsure of the legitimacy of an email, please contact VCU IT Support Center (828-2227), or your local IT staff, they can help you verify the legitimacy of the email. Alternatively, the VCU Information Security Team can also help you to check the authenticity of an email.
To report any phishing email, please contact the VCU Information Security Team or VCU IT Support Center at 828-2227.
This article was updated: 09/9/2024